We value your privacy!
We use cookies on our website to offer you the best experience. By clicking "accept & close", you agree to the use of all cookies according to our and our . If you do not make a selection, our default cookie settings will be applied. You can change your settings at any time.
Essential cookies: They are required for the proper functioning of the website. First-party- und third-party-cookies: They are optional and are set by us or our subcontractors. Session and persistent cookies: Are automatically deleted when the browser is closed. Persistent cookies are cookies that remain on your computer/device for a certain period of time after the browser is closed.
Creating a digital signature - How to obtain a (qualified) electronic signature (QES)
When you need a qualified electronic signature, you often come across the terms "identification" and "authentication". But what do these terms mean? And why do I need it when signing digitally? How do I get a QES and how does the identification process work? In this article we clarify!
Updated on 28.02.2023
What is identification? Establishing identity via video identity
In order to ensure that the document has been signed by the correct person when signing it digitally, the person's identity must be verified. If, for example, only an image of the signature is placed on a document, the identity cannot be verified and ensured. Therefore, a qualified signature is required on important documents to maximize the probative value and legal validity. In order to sign with a qualified electronic signature (QES), one must go through an identification process once...
Identification is the process of establishing one's own identity. In most cases, this is done by presenting an official identification document (e.g. passport or ID card). For example, when opening a bank account, the identity is verified by comparing the biometric features of the photo ID shown with the natural person standing in front of the bank employee or present via video call. Identification only needs to be performed once at the time of registration.
In our case, the user is identified before a qualified electronic signature is obtained. This can be done, for example, online at a trust service provider of your choice using a video identification procedure (Videoident). In this process, personal data must be entered beforehand and, in the case of a video call, a photo ID must be presented. If the data provided matches the ID data and the biometric data from the photo ID matches the person in the video call, the identity can be verified.
What is authentication?
After you have been identified and "know" yourself, you "only" have to authenticate yourself from now on. During authentication, you have to prove your identity every time. This can be done using various authentication factors. For example
- a password/PIN (knowledge)
- a smartphone that can receive one-time verification codes or
- a fingerprint scan/Face ID (biometrics).
The factors can also be combined, such as in two-factor authentication and multi-factor authentication, to increase security.
Authentication is therefore the verification of a given identity. Two-factor authentication comes into play in qualified signing. After logging in to sproof sign (factor 1 password), qualified signing requires you to confirm your identity using a mobile app (factor 2 fingerprint or Face ID).
Identification vs. authentication - what is the difference?
Identification establishes the identity of a person and links the digital identity to a natural person and their name. Identification only needs to be performed once as the first step, e.g. user registration with sproof sign or identification procedures to obtain a QES.
During authentication/authentication, the identity is proven. In this process, the given identity is compared with the given data. This authentication process must be performed again each time, e.g., logging in with sproof sign or 2-factor authentication when signing with QES.
Identification and authentication thus go hand in hand and cannot work without the other.
Identification and authentication for qualified signing
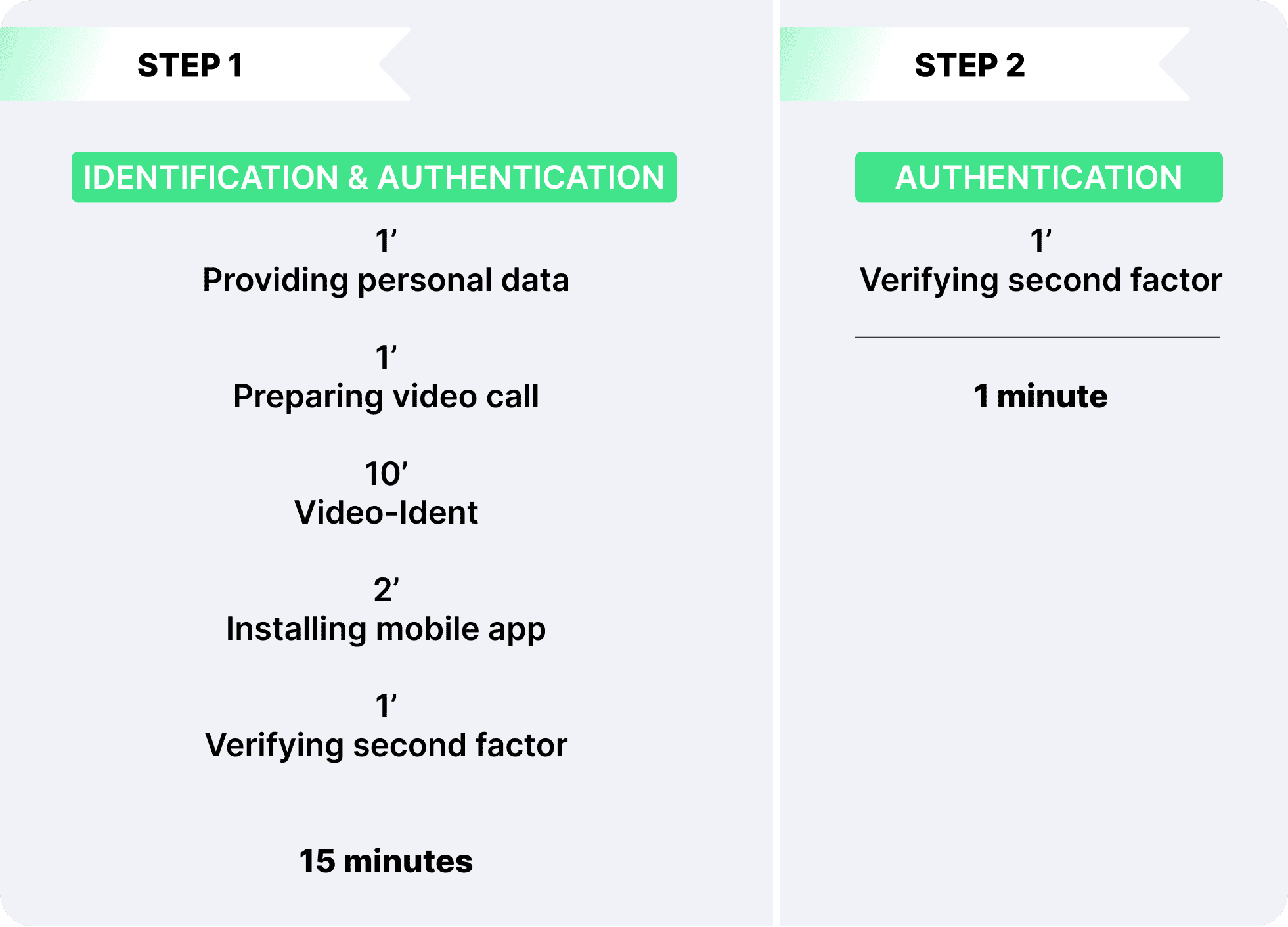
In short, to obtain a qualified electronic signature (QES), you have to identify yourself once and set up 2-factor authentication (duration: 15 minutes once). For qualified signing, one then only has to authenticate (duration: <1 minute each time).
How do I get a QES (at sproof sign)?
- To get a QES, you must first provide your personal information
- Before you start the video identification procedure, you have to present your official photo ID
- In the video call you have to show your official photo ID. As a result, the trusted service provider will compare your provided data with the ID card data and the biometric data from the photo ID with you in the Video Call. If all the information matches, your identity is verified.
- Next, you need to download a mobile app (e.g. Mobile ID) and log in.
- In the app, your digital identity is stored by the trust service provider and a second security factor (e.g. fingerprint scan or Face ID) is set up.
- From now on, you can sign qualified and only need to authenticate in the app (push message) before signing qualified.
More blog entries
Team Axess chooses digital signature solution from sproof signPrivate banking in transition - Bank Gutmann relies on digital signatureConstantin Graf from Vienna compares software tools "Made in Europe".Digital contracts, real commitment: the FSJ and the path to paperless administration"sproof helps us to combine security and efficiency" - Dominik Engel, FH Salzburg

